video doodle, doodle awek, doodle awek cun,doodle bertudung, doodle muslimah, doodle terhangat, doodle percuma, doodle free,doodle cantik,tutorial illustrator, tutorial photoshop, tutorial autodesk maya, tutorial flash, cerita kartun, cerita sosial, informasi terkini, tips blog, tutorial blog, trick blog, tips traffic blog, cara buat doodle, doodle illustrator
Memaparkan catatan dengan label Notes. Papar semua catatan
Memaparkan catatan dengan label Notes. Papar semua catatan
29 September 2011
20 September 2011
LAB 2: The Goals of Information Technology Security
LAB 2: The Goals of Information Technology Security
23 Mac 2011
Peer-To-Peer Networking
Review Questions
1. Find 2 P2P file sharing applications that use centralized directory other than
Napster.
I. Audiogalaxy
II. Direct Connect
III. Advanced Direct Connect
IV. Soulseek
V. Opennap
VI. Soribada
2. Find 2 P2P file sharing applications that use decentralized directory other than
KaZaa.
I. Applejuice
II. Ares
III. BitTorrent
IV. eDonkey
V. FastTrack
VI. Freenet
3. Find 2 P2P file sharing applications that use query flooding other than Gnutella.
I. WinMX
II. Limewire
III. eMule
IV. Bearshare
4. List 3 open source-based P2P file sharing applications.
I. QuteCom : Free Voice, Video and IM client application
II. Icecast : open source streaming media server
III. YaCy : P2P-based search engine
IV. TVmad : p2p free online streaming
V. Radiolicious: Internet radio
5. List 3 proprietary-based P2P file sharing applications.
I. MetaMachine (eDonkey2000 )
II. Loophole (WinMX protocol)
III. KCeasy is client based on giFT peer to peer file sharing protocol
6. Make a search on P2P file sharing applications. Among all P2P services (other than
Ares), which one caught your interest the most? Explain why (interface, features,
add-ons, performance, license type, ratings etc.)
I choose WinMX because WinMX one of pretty old peer to peer file sharing program has suffered due to lowsuite and its official website and server is now offline form 2005 although WinMX program is still operating successfully.WinMX network has limited number of Viruses and also it has restriction of maximum file size can be shared is 2 GB only.WinMX is majorly used for audio and video file sharing but you can use it for sharing any types of files. Also Supported Operating system: Win XP/NT 4.x/2003/2000/Vista.
License type is freeware.
Rating review is 5 star.
1. Find 2 P2P file sharing applications that use centralized directory other than
Napster.
I. Audiogalaxy
II. Direct Connect
III. Advanced Direct Connect
IV. Soulseek
V. Opennap
VI. Soribada
2. Find 2 P2P file sharing applications that use decentralized directory other than
KaZaa.
I. Applejuice
II. Ares
III. BitTorrent
IV. eDonkey
V. FastTrack
VI. Freenet
3. Find 2 P2P file sharing applications that use query flooding other than Gnutella.
I. WinMX
II. Limewire
III. eMule
IV. Bearshare
4. List 3 open source-based P2P file sharing applications.
I. QuteCom : Free Voice, Video and IM client application
II. Icecast : open source streaming media server
III. YaCy : P2P-based search engine
IV. TVmad : p2p free online streaming
V. Radiolicious: Internet radio
5. List 3 proprietary-based P2P file sharing applications.
I. MetaMachine (eDonkey2000 )
II. Loophole (WinMX protocol)
III. KCeasy is client based on giFT peer to peer file sharing protocol
6. Make a search on P2P file sharing applications. Among all P2P services (other than
Ares), which one caught your interest the most? Explain why (interface, features,
add-ons, performance, license type, ratings etc.)
I choose WinMX because WinMX one of pretty old peer to peer file sharing program has suffered due to lowsuite and its official website and server is now offline form 2005 although WinMX program is still operating successfully.WinMX network has limited number of Viruses and also it has restriction of maximum file size can be shared is 2 GB only.WinMX is majorly used for audio and video file sharing but you can use it for sharing any types of files. Also Supported Operating system: Win XP/NT 4.x/2003/2000/Vista.
License type is freeware.
Rating review is 5 star.
4 Mac 2011
Introduction To Computer Graphics
What is Computer Graphic?
• the term "computer graphic" was coined in 1960 by William Fetter
• to describe new methods he was pursuing at Boeing
• mean the creation, storage and manipulation of model and images; all generated by computer
• computer graphic are picture or images generated by computer.
4 Main Task:
• Software Tools: OpenGL; write program to create images
• Software For CGI Animation: 3Dstudio Max/ Maya/ Blender
Element of Computer Graphic System
• processor; memory; frame buffer(memory store of pixel)
• input device; output devices(CRT)
• the term "computer graphic" was coined in 1960 by William Fetter
• to describe new methods he was pursuing at Boeing
• mean the creation, storage and manipulation of model and images; all generated by computer
• computer graphic are picture or images generated by computer.
Modelling And Rendering
• modelling: develop a mathematical representation of any 3D surface of object.
• method: implicit func. ; polygon mesh; splines; metaballs
• representing a scene or object in a format that can be stored in computer memory
• rendering: give final appearance to the model; 2D to 3D; technique=raytracing
• method: implicit func. ; polygon mesh; splines; metaballs
• representing a scene or object in a format that can be stored in computer memory
• rendering: give final appearance to the model; 2D to 3D; technique=raytracing
 |
| metaballs |
- Imaging: representing 2D Images
- Modelling: creating and representing the geometry of object in the 3D world
- Rendering: constructing 2D images from 3D model
- Animation: describing how objects change in time
Computer Graphic Tool
• Hardware Tool: video monitor; graphic cards; data gloves; graphic tablet• Software Tools: OpenGL; write program to create images
• Software For CGI Animation: 3Dstudio Max/ Maya/ Blender
Where CGI (computer graphic interface) are used?
• computer games; movie production; animation and special effect; slide, book, megazine design
• monitoring a process: air traffic control system
• simulations: flight simulator
• computer aided design(CAD)
• processor; memory; frame buffer(memory store of pixel)
• input device; output devices(CRT)
Transformation: encoded as 4x4 matrix
Clipping: limited field of view so cut geometry against the clippilng rectangle
Projection: flatten object from 3D to 2D
Rasterization: (scan conversion): covert geometry primitives(lines, polygon) to pixel
Geometric Objects And Transformation (Part 2)
Transformations
• one example of a transformation is the windows to view port transformation
• to allow us to move objects to more complex locations
• OpenGL pipeline makes transformations easy
• transformation consists of (occur in 2d and 3d)
• a rotation
• a scaling
• a translation
• a shearing
• transformation allow for:
2. Scaling : This means that x, y and z coordinates are being multiplied by a scalar
3. Rotation : This means that x,y,z rotated araound a point
4. Shearing : That a point is dragged in a particular direction, coordinated affected but other are not
5. Combining Transformation : rotate scaling, translation and shearing can be combined into matrix
• one example of a transformation is the windows to view port transformation
• to allow us to move objects to more complex locations
• OpenGL pipeline makes transformations easy
• transformation consists of (occur in 2d and 3d)
• a rotation
• a scaling
• a translation
• a shearing
• transformation allow for:
- scene composition
- easily create symmetrical object
- viewing object at different angles
- computer animation where several objects need to more relative to one another
• Transformation points ( simply takes a point and maps it to another location)
 |
| transformation point |
• Affine Transformations : there are 4 types of transformations that can be combined to produce an affine transformation
- Translation: moving point/object around in the x,y, and z direction
 |
| This means that values are being added or subtracted to the existing coordinates |
 |
| Scale point; P = (6,2) to Q = (3,4) |
3. Rotation : This means that x,y,z rotated araound a point
 |
| rotation matrix |
Input And Interaction
Input Device
• physical device
• logical device : define the type of input; not adopted in openGL
Classes of Logical Device
A SIMPLE PAINT PROGRAM
Requirements:
• physical device
• logical device : define the type of input; not adopted in openGL
 |
| input device |
- String Device : returns strings of characters; physical device keyboard
- Locator: returns; physical device mouse
- Pick: returns the ID of the graphical object; physical device mouse button gun
- Choice: mouse returns one of a discrete number of option;ex menu
- Stroke: return array of location; similar to locator; ex push button, releasing the button mouse
Input Process
- Measure process: input device returns a set of logical measures
- Trigger process: input device returns the trigger signal
Input Modes
 |
| Request mode: |
 |
| Sample mode: |
 |
| Event mode: |
Display Lists
- is a compiled list of intructions stored in adisplay memory(client) or on a graphics server
A SIMPLE PAINT PROGRAM
Requirements:
- Draw geometric objects.
- Manipulate pixels.
- Control attributes, such as color, line type,
- and fill patterns.
- Include menus.
- Allow for moving and resizing the window
3 Mac 2011
Overview Of The Internet
Autonomous System
• the infrastructure of the internet each independently managed
• each may consist of multiple network
• each have number called AS number
Internet Access Method
• Dial-up : use a modem and standard telephone line (max speeed not exceed=56kbps)
• ISDN : use existing telephone lines (allows 64Kbps on a single channel). Two channel = 128Kbps.
• DSL : use existing telephone lines, using DSL hub; always connected ; (640Kbps>speed>256Kbps)
• Cable Modem: use existing TV coaxial cable;
provide by cable TV provider; via network card and ethernet cable; speed<1.5Mbps
T-1/DS-1
• very specialized telecommunication circuit that does not work over normal telephone line
• divide in 24 channels in many different purpose; speed<1.54Mbps
How An Internet Service Provider Works
• after connect to ISP by cable, DSL or telephone line the ISP connect you to the internet
• a router device that connect two or more network can make decision about the best way to route data over these networks
• Region network=Wide Area Network (WAN); a network covers a large geographical area.
• Channel Service Unit(CSU) acts as a safe electrical buffer between the LAN and public network
• Digital Service Unit or Data Service Unit; data formatted correctly before allowed on the T1 line
Point Of Presence
• is a connection point to the internet; either a telephone number, Dial-up
Uniform Resource Locator
• is an address for a web page file or other resource on the internet
Internet
• consist of a large number of computer connected or network to each other
• server tend to have greater capacity and more expensive
Intranet
• a network that uses the TCP/IP protocol to provide private services within an organization.
• medium or larger business enterprise
Extranet
• refer to internet resource that are beyond the reach of the public and require login name and password to access
• certain large or privileged customers; suppliers and subcontractor
• the infrastructure of the internet each independently managed
• each may consist of multiple network
• each have number called AS number
Internet Access Method
• Dial-up : use a modem and standard telephone line (max speeed not exceed=56kbps)
• ISDN : use existing telephone lines (allows 64Kbps on a single channel). Two channel = 128Kbps.
• DSL : use existing telephone lines, using DSL hub; always connected ; (640Kbps>speed>256Kbps)
• Cable Modem: use existing TV coaxial cable;
provide by cable TV provider; via network card and ethernet cable; speed<1.5Mbps
T-1/DS-1
• very specialized telecommunication circuit that does not work over normal telephone line
• divide in 24 channels in many different purpose; speed<1.54Mbps
Internet Service Providers (ISPs)
• a bussiness that provides connectivity to the internet
• can be a small bussiness hat provides connectivity in only one city, or large company with access points in
many cities and country
• Popular ISPs
• can be a small bussiness hat provides connectivity in only one city, or large company with access points in
many cities and country
• Popular ISPs
- TMNet
- Jaring
- School And College Network
Primary Purpose of an ISP
To Connect To The Internet:
- a physical connection
- software to communicate
- an address
To Connect To An ISP
• must be using an operating system that support communication protocol such TCP/IP
Local Area Network (LAN)
• a group of computer and other devices network together that is confined in a small area
How An Internet Service Provider Works
• after connect to ISP by cable, DSL or telephone line the ISP connect you to the internet
• a router device that connect two or more network can make decision about the best way to route data over these networks
• Region network=Wide Area Network (WAN); a network covers a large geographical area.
• Channel Service Unit(CSU) acts as a safe electrical buffer between the LAN and public network
• Digital Service Unit or Data Service Unit; data formatted correctly before allowed on the T1 line
Point Of Presence
• is a connection point to the internet; either a telephone number, Dial-up
Uniform Resource Locator
• is an address for a web page file or other resource on the internet
Internet
• consist of a large number of computer connected or network to each other
• server tend to have greater capacity and more expensive
Intranet
• a network that uses the TCP/IP protocol to provide private services within an organization.
• medium or larger business enterprise
Extranet
• refer to internet resource that are beyond the reach of the public and require login name and password to access
• certain large or privileged customers; suppliers and subcontractor
Geometric Objects And Transformation (Part 1)
Three Basic Types
• scalars
• points
• vectors
Define this in three different ways:
• geometric view
• point-a location in space
• scalar-unit of measurement, real numbers
• vector-quantity with direction and magnitude
• mathematical view
• linear vector space - combine 2 distinct scalar and vectors
• affine space - adds the point, operation=vector point addition; point-to-point subtraction.
• euclidean space - add concept of distance
• computer science view
• Abstract Data Type (ADTs) = set of operation on data.
• fundamental to modem computer science
• scalars
• points
• vectors
Define this in three different ways:
• geometric view
• point-a location in space
• scalar-unit of measurement, real numbers
• vector-quantity with direction and magnitude
• mathematical view
• linear vector space - combine 2 distinct scalar and vectors
• affine space - adds the point, operation=vector point addition; point-to-point subtraction.
• euclidean space - add concept of distance
• computer science view
• Abstract Data Type (ADTs) = set of operation on data.
• fundamental to modem computer science
1 Mac 2011
Presentation Layer
Presentation Layer
• is the sixth level of OSI model
• sender and receiver seeing same data = presentation format.
• presentation layer may be represent(encode) the data in various way; ex: data compression,or encryption
• convert into its original meaning
Specific Reponsibilities Of Presentation Layer
• Data Representation
XDR
• Sun Microsystem's External Data Representatin(XDR) is much simpler than ASN.l but less powerful.
1. XDR uses implicit typing
2. all data transfered in units of 4 bytes
• Data Compression
Image Compression
Encryption
• sender transform original information(plaintext) to another form(ciphertext)
• is the sixth level of OSI model
• sender and receiver seeing same data = presentation format.
• presentation layer may be represent(encode) the data in various way; ex: data compression,or encryption
• convert into its original meaning
• Data Representation
- different computer=different representation for character
- converting the complex data structures used by application into a byte stream trasmit across the network.
- Popular network data reprentations include:
- • ASN.l - an ISO standard
- • XDR - used with SunRPC
• Abstract Syntax Notation (ASN.l) that address the issue of representing, encoding , transmitting and decoding data structure
• Two part:
1. Abstract Syntax: that describe data structure in an unambiguous way. use int; string;
2. Transfer Syntax: that describes the bit stream encoding of ASN.l data object
The main reason for success of ASN.l is that it is associated with several standardized encoding rules such:
• Basic Encoding Rules(BER) - X.209
• Canonical Encoding Rules(CER)
• Distinguised Encoding Rules(DER)
XDR
• Sun Microsystem's External Data Representatin(XDR) is much simpler than ASN.l but less powerful.
1. XDR uses implicit typing
2. all data transfered in units of 4 bytes
• Data Compression
- Lossless Compression: data is compressed and can be uncompressed
- Lossy Compression: aim to obtain the best possible fidelity for given bit-rate. most suite to video and audio compression techniques
• Why Compression:
- need to compress the data at the sender and decompress it at the receiver
- storage can be efffectively increased
- communication link can be effectively increased
 |
| step of data compression |
• to represent image with less data in order to save storage or transmission time
• possible to reduce file size to 10% from original without noticeable loss in quantity
Lossless -image quality is not reduce: ex; drawing, graphic, logo
method: Run-Length Encoding(RLE), Huffman CodingLossy- reduce image quality.cannot get the original image back and lose some information
ex: natural image such a photo landscape. method: Dicrete Cosine Transform(DCT)Audio Compression
• a form of data compression design to reduce the size of audio files
• audio compression can be lossless or lossy compression
• audio compression algoritm are typically refered to as audio codecs
Lossless - allows one to preserve an exact copy of one's audio files
codec: Apple Lossless, Free Lossless Audio Codec(FLAC)
Lossless Predective Audio Compression(LPAC), (LTAC)
Lossy - irreversible changes, achive for greater compresion
codec: MP3, MP2, WMA
Video Compression
• storing and transmitting uncompressed raw video is not an efficient technique
because it needs large amount of storage and bandwidth
• DVD, DSS use digital data: take a lot of space to store and large bandwidth to transmit
• less storage space=less bandwidth to transmit data
• inter frame=using its predecessor
• intra frame=coded independently
Video Compression Techniques
1. flow control and buffering
2. temporal compression
3. spatial compression
4. discrete cosine transform (DCT)
• a form of data compression design to reduce the size of audio files
• audio compression can be lossless or lossy compression
• audio compression algoritm are typically refered to as audio codecs
Lossless - allows one to preserve an exact copy of one's audio files
codec: Apple Lossless, Free Lossless Audio Codec(FLAC)
Lossless Predective Audio Compression(LPAC), (LTAC)
Lossy - irreversible changes, achive for greater compresion
codec: MP3, MP2, WMA
Video Compression
• storing and transmitting uncompressed raw video is not an efficient technique
because it needs large amount of storage and bandwidth
• DVD, DSS use digital data: take a lot of space to store and large bandwidth to transmit
• less storage space=less bandwidth to transmit data
• inter frame=using its predecessor
• intra frame=coded independently
Video Compression Techniques
1. flow control and buffering
2. temporal compression
3. spatial compression
4. discrete cosine transform (DCT)
Encryption
• sender transform original information(plaintext) to another form(ciphertext)
• to carry sensitive information, a system must be abe to assure privacy
• to protect information
• done in presentation layer besides transport and physical layer
Decryption
• reverse the original process to transform the message(ciphertext back to original(plaintext)
• to protect information
• done in presentation layer besides transport and physical layer
Decryption
• reverse the original process to transform the message(ciphertext back to original(plaintext)
26 Februari 2011
OpenGL Programming Part 2
The Sierpinski Gasket
• generated using randomly selected vertices
• is fractal, an object that can recursively and randomly;
Attributes
• an attributes is any property that determines how a geometric primitives is to be rendered
• color
-thickness
-pattern
• styles
-bold, italic, line
-string, height, weight
Color
• color model is an orderly system for creating a whole range of color from a small set of primary colors
• solid color
• two types of color models:
-Additive
-Subtactive
4 channels:Red, Green, Blue and Alpha (opacity/transparency).
• Each channel has intensity from 0.0 ~ 1.0
• Alpha is used in blending and transparency
• Ex: glColor4f(0.0, 1.0, 0.0, 1.0); //green
glColor4f(1.0, 1.0, 1.0, 1.0); //white
• generated using randomly selected vertices
• is fractal, an object that can recursively and randomly;
Attributes
• an attributes is any property that determines how a geometric primitives is to be rendered
• color
-thickness
-pattern
• styles
-bold, italic, line
-string, height, weight
Color
• color model is an orderly system for creating a whole range of color from a small set of primary colors
• solid color
• two types of color models:
-Additive
- RGB Color Model
- Use light to display color
- red+green+blue = white
-Subtactive
- CMY Color Model
- substractive model using printing ink
- color result from reflected light
- cyan+magneta+yellow = black.
 |
| Color Model |
 |
| Color Range |
• Each channel has intensity from 0.0 ~ 1.0
• Alpha is used in blending and transparency
• Ex: glColor4f(0.0, 1.0, 0.0, 1.0); //green
glColor4f(1.0, 1.0, 1.0, 1.0); //white
OpenGL Programming Part 1
What is OpenGL®
• graphic rendering Application Programming Interface
• high quality color images composed of geometric and image primitives
• window and operating system independent
• a library for 3D graphic and modelling
• portable and fast
• coordinate transform
• anti-aliasing
• pixel update operation
• display list
OpenGL® Primitives
• All geometric object in OpenGL are created from a set of basic primitives
• certain primitives are provided to allow optimization of geometry for improved rendering speed.
OpenGL Supports:
• graphic rendering Application Programming Interface
• high quality color images composed of geometric and image primitives
• window and operating system independent
• a library for 3D graphic and modelling
• portable and fast
 |
| The OpenGL Pipeline |
The OpenGL® Standard
• an API not a language
• some graphic package include
- Renderman
- Renderware
- DirectX
What can OpenGL® do?
• display primitives• coordinate transform
• anti-aliasing
• pixel update operation
• display list
OpenGL® Primitives
• All geometric object in OpenGL are created from a set of basic primitives
• certain primitives are provided to allow optimization of geometry for improved rendering speed.
 |
| Line Based Primitives |
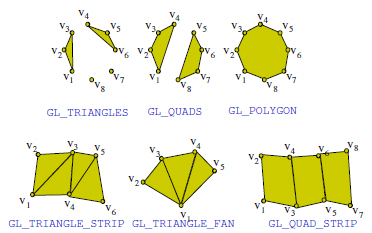 |
| Polygon Primitives |
• phong illumination model
-diffuse reflection
-phong specular highlight
-ambient illumination
• shading models
-flat shading
-gourand shading
-phong shading
Relevent Library
• the GL library : core function of OpenGL; modelling, viewing, clipping, lighting
• The GL Utility (GLU) : create common object; sphere quadrics : special of standard views; perspective, orthographic
• The GL Utility Toolkit (GLUT) : provides the interface with the windowing system.
• window management, menus, mouse interaction
 |
| OpenGL Command Format |
25 Februari 2011
TELNET
TELNET
• is a standard TCP/IP protocol for virtual terminal service
• this client-server application program enables the estabalisment of a connection to a remote system whereby the local terminal appears to be a terminal at the remote system
• Windows versions also include Telnet Client and Telnet Server Component
Initiating And Using Telnet Session
Telnet Enable user:
• create remote command console session on a host
• run command line programs, shell commands, and script in aremote command console session
How Telnet Works
• To use Telnet you need to know IP adress of the host where the resource you want use
• When you contact the host; the distant computer and your computer negotiate how to communicate with each other
• When client and server communicate they use Telnet protocol
• You start manually / configure automatic every time you want to connect to a host
Telnet In Windows XP
• Use Run dialog box
type: telnet mydomain.com
• Use Web browser
Enter: telnet://mydomain.com
Example of Telnet Client/Server
• Tlntsvr.exe(Telnet server) - preinstalled in windows os
• Telner.exeITelnet server) - preinstalled in windows ps
Telnet Limitation
• not design to transmit cursor movement or GUI information
• can only run command line programs, shell, commands, script, and batch files
• does not encrypt any data sent over the connection
Using Secure Shell Protocol (SSH)
• enable two computer to negogiate and estabalish secure connection that use encryption
• may stop cracker who try to sniff password and data
• provide secure communication for doing email and access web.
• is a standard TCP/IP protocol for virtual terminal service
• this client-server application program enables the estabalisment of a connection to a remote system whereby the local terminal appears to be a terminal at the remote system
• Windows versions also include Telnet Client and Telnet Server Component
Initiating And Using Telnet Session
Telnet Enable user:
• create remote command console session on a host
• run command line programs, shell commands, and script in aremote command console session
How Telnet Works
• To use Telnet you need to know IP adress of the host where the resource you want use
• When you contact the host; the distant computer and your computer negotiate how to communicate with each other
• When client and server communicate they use Telnet protocol
• You start manually / configure automatic every time you want to connect to a host
 |
| TELNET Software |
• Use Run dialog box
type: telnet mydomain.com
• Use Web browser
Enter: telnet://mydomain.com
Example of Telnet Client/Server
• Tlntsvr.exe(Telnet server) - preinstalled in windows os
• Telner.exeITelnet server) - preinstalled in windows ps
Telnet Limitation
• not design to transmit cursor movement or GUI information
• can only run command line programs, shell, commands, script, and batch files
• does not encrypt any data sent over the connection
Using Secure Shell Protocol (SSH)
• enable two computer to negogiate and estabalish secure connection that use encryption
• may stop cracker who try to sniff password and data
• provide secure communication for doing email and access web.
File Transfer And Remote File Access
File Transfer Protocol (FTP)
• standard mechanism provided by TCP/IP for copying file from one host to another.
• FTP Site is a computer running an FTP server Application
• On FTP Server, a program called daemon allows to download and upload files
• FTP can transfer binary files over internet without encoding and decoding overhead
• FTP can upload files from your computer to another computer
• Large organization use mirror site; contain same set of files
• Mirror site serve as a backup for the main server if main server fails
How FTP Works
• FTP server identifies user based on user IDs
• FTP client / server create a session after you are logged on
• FTP client has access to the file system on the server
• FTP cliend / server software can access their individual file system in either direction
Requirement For Using FTP
TFTP Usage And Design• Transfer files between process.
• Minimal overhead(no security)
• Easy to implement
• Small-possible to include firmware
• Used to bootstrap workstations and network devices.
TFTP Protocol
• standard mechanism provided by TCP/IP for copying file from one host to another.
• FTP Site is a computer running an FTP server Application
• On FTP Server, a program called daemon allows to download and upload files
• FTP can transfer binary files over internet without encoding and decoding overhead
• FTP can upload files from your computer to another computer
• Large organization use mirror site; contain same set of files
• Mirror site serve as a backup for the main server if main server fails
How FTP Works
• FTP server identifies user based on user IDs
• FTP client / server create a session after you are logged on
• FTP client has access to the file system on the server
• FTP cliend / server software can access their individual file system in either direction
• FTP uses two well known port:
- Port 20 for data connection
- Port 21 for control connection
 |
| BASIC MODEL OF FTP |
- An FTP client installed on the computer.
- Login details of the FTP server to which you want to connect:
- The FTP server address. This looks a lot like the address you type in Internet Explorer to browse websites. One such example is “ftp://ftmk.utem.edu.my”.
- The user name and password required for the FTP connection. Some FTP servers let you connect to them anonymously. For anonymous connections, you do not need a user name and password.
FTP From A Command Prompt
• Another similar FTP is TFTP (Trivial FTP)
• TFTP has fewer command than FTP
• TFTP used only to send and receive files.
• It can be used for multicasting which a file is sent to more than one client at the same time using UDP
TFTP Usage And Design• Transfer files between process.
• Minimal overhead(no security)
• Easy to implement
• Small-possible to include firmware
• Used to bootstrap workstations and network devices.
TFTP Protocol
- • Read request
- • Write request
- • Data
- • ACK(acknowledgement)
- • Error
Langgan:
Ulasan (Atom)